Malwarebytes For Mac Won't Allow Extension
Malwarebytes does not fix issues you may be experiencing with your web browser or Internet connectivity. If you're experiencing issues with your browser or Internet connection, you may need to restore your browser or Internet connection manually. Malwarebytes AntiMalware for Mac (formerly AdwareMedic). However, is a different story. It's recommended by Apple support procedures as a good adware/malware removal tool.
Malwarebytes For Apple Mac
However, the number of Mac users infected by malware and other Mac threats has had exponential growth since 2010, when adware and PUPs weren’t really a thing on the Mac yet and when new malware sightings were few and far between. We’re seeing large numbers of people infected with Mac threats every day, on a much larger scale than even just a few years ago.
Opened Safari. Restarted Safari, black screen. No sites opened. Opened Chrome, no issues, worked fine. Mail worked, Photo's didn't sync.
Malwarebytes Anti-malware won’t run 2.1 Rename the main executable file Click Start, type in Search field%ProgramFiles% (if you using Windows 2000/XP, Click Start, Run, then type in Open field) as shown below. It will open a contents of ProgramFiles folder. Next, open Malwarebytes Anti-Malware folder. Right-click on the mbam.exe file and select Rename option as a screen below. Type explorer.exe and press Enter. Double-click on it to run. Best for cad mac or pc 2017.
Malwarebytes Browser Extension
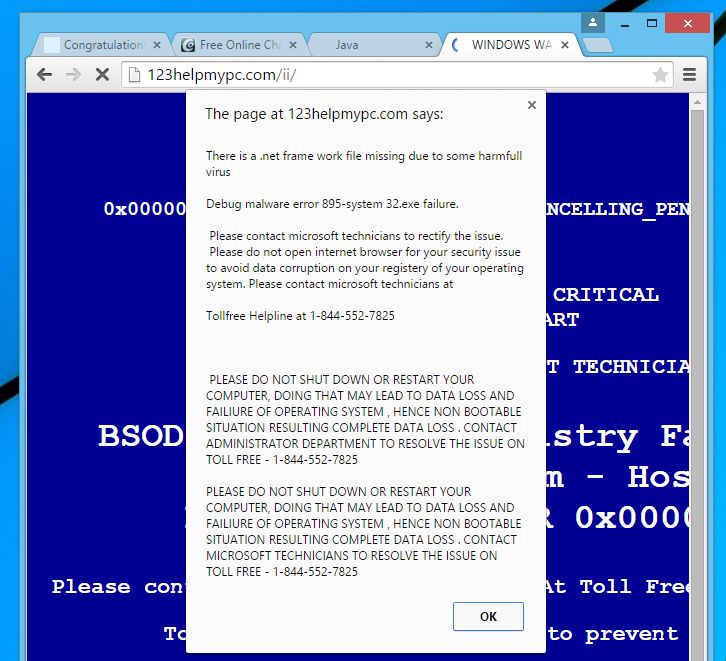
The origin of such infections can never be traced unless once being infected by it. The unpredictability of the threat is so enormous in nature that, even it could come from official white-collar companies. The software’s become malware only when it goes against the interests of the user. This, it will do secretly, hence making it harder for any anti-virus to root out the malware. Sixty-nine percent of most malware are trojans. Trojans are malware which enters the user’s workspace without raising any red flags. But, as soon as it’s in the trojan kicks into full gear and starts to contact a controller.